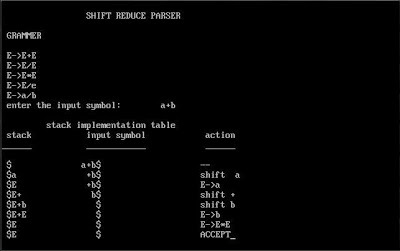
To implement local search algorithm for Travelling Salesman Problem using Hill Climb > Java Program
To implement local search algorithm for Travelling Salesman Problem using Hill Climb > Java Program Artificial Intelligence Program: package javaapplication5; import java.util.*; public class JavaApplication5 {